- Backend Developers
- Frontend Developers
- Database Developers and so, on…
Are Bubble Applications Secure?
When we want to build an application on any platform, our first concern is “Is my application and data secure?” or “Is the chosen platform reliable?”
Bubble’s official document explains,
Bubble protects your developed app and data using industry best practices. All apps produced on the Bubble.io platform benefit from the Bubble’s security investment.
Below is the list of some areas where Bubble provides security while Application Development:
- Hosted on secure cloud ( Amazon Web Services )
- Monitoring and Testing
- Data Loss Recovery
- Server Logs
- RDS AES-256 encryption
- User-defined privacy
Amazon Web Services
As Bubble explains, “Bubble is using wed services of the AWS during application development”. AWS web services are compliant with certifications like SOC 2, CSA, ISO 27001, and more.
Service Organization Controls 2 (SOC 2): SOC 2 is developed by the American Institute of CPAs (AICPA). It is responsible for the compliance standard for service organizations. The main purpose of this compliance is to specify how organizations should manage customer data.
- Compliance, Safety, Accountability (CSA): Compliance, Safety, Accountability (CSA) compliance is defined by the Federal Motor Carrier Safety Administration (FMCSA).
- ISO 27001: ISO 27001 is the international standard for information security. The main reason for this compliance is that it will help you avoid security-related threats. It sets out the specification for cybercriminals breaking into your organization.
Monitoring & Testing
The Bubble itself uses automated code testing, vulnerability testing (including OWASP Top 10), and tools for continuous monitoring of the app code. OWASP stands for “Open Web Application Security Project”. It is a nonprofit organization that works in web application security. The OWASP Top 10 is a list of the 10 most critical web application security risks. Below are the security risks listed in the OWASP Top 10 2017 report:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XEE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
The Bubble.io itself uses automated code testing, vulnerability testing (including OWASP Top 10), and tools for continuous monitoring of the app code. OWASP stands for “Open Web Application Security Project”. It is a nonprofit organization that works in web application security. The OWASP Top 10 is a list of the 10 most critical web application security risks. Below are the security risks listed in the OWASP Top 10 2017 report:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XEE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
Data Loss Recovery
Bubble ensures that if a user deletes important application data inadvertently, she could recover data loss. How far back in time you delete your application’s important data you can go will depend on your active plan.
To copy and restore database you have to switch into the App Data section of the Data tab, in App Data section click on the Copy and restore database link.
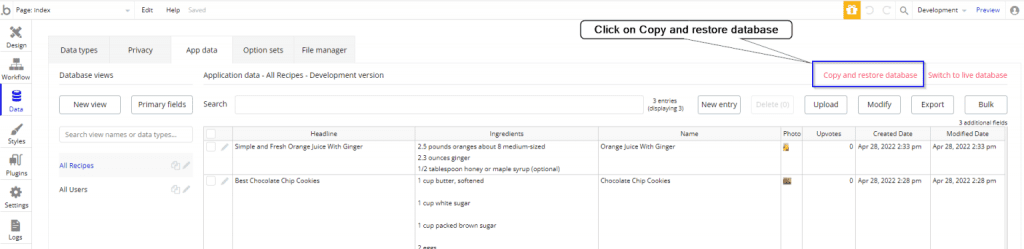
After clicking on Copy and restore database below popup will open. In this popup you can perform copy and restore database related operations.
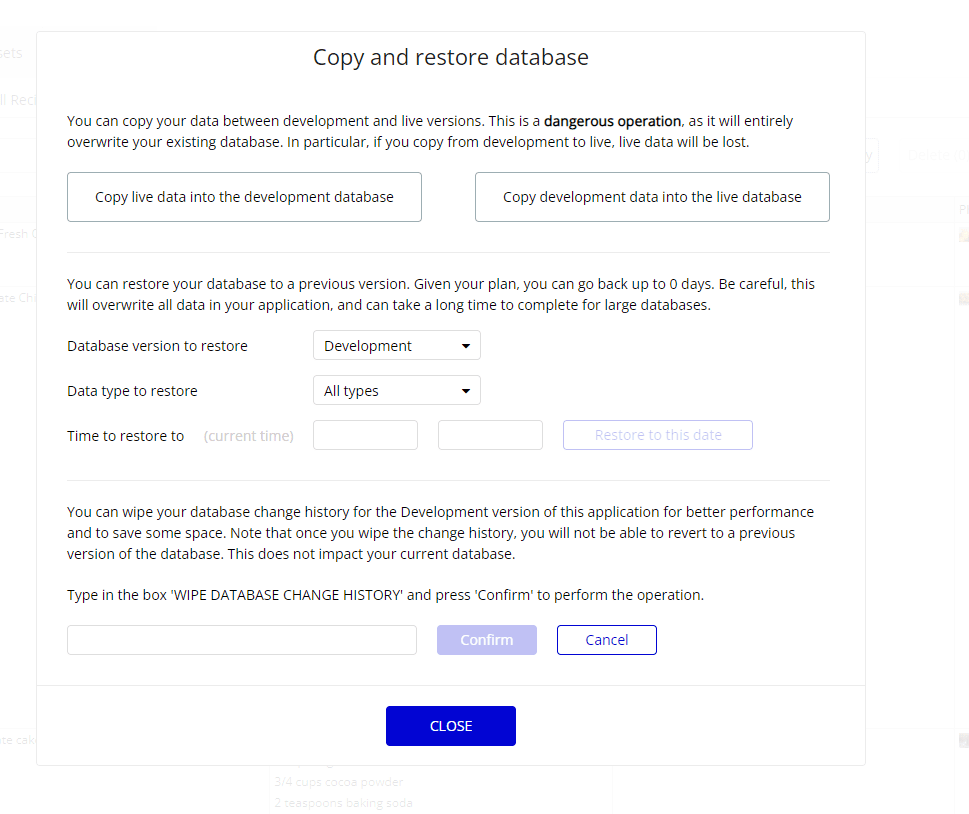
A place for big ideas.
Reimagine organizational performance while delivering a delightful experience through optimized operations.

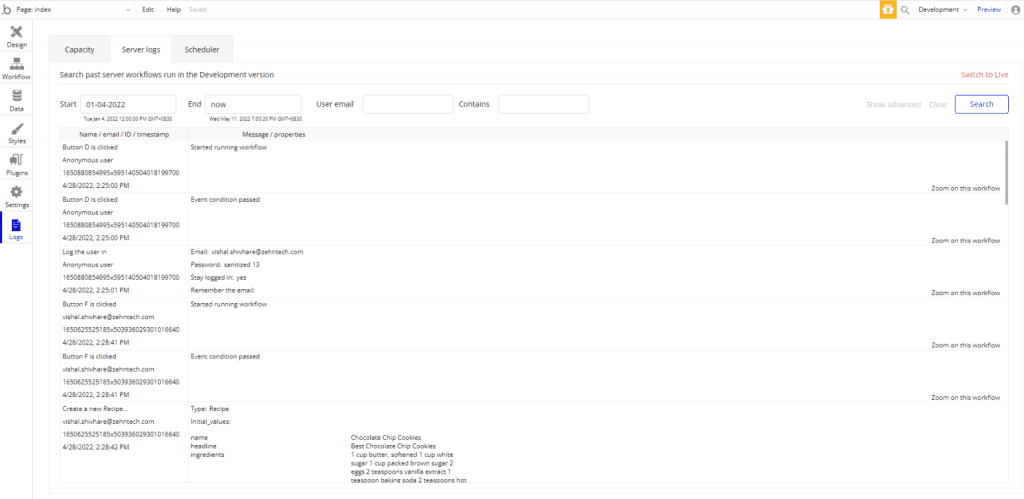
Server Logs
Bubble apps maintain extensive logs for data change and application functions too. So, you can check any time what has been done in your app. Also, Bubble actively creates logs in the background for your application, so you can check what is going on in your app. with the help of the server logs you to explore issues related to your application in the past.
In the Server Logs section of the Logs tab, you can search for the log of server-side actions. Also, you can search for a particular user ID or name, specific dates, or specific keywords.
RDS AES-256 Encryption
Bubble uses AWS RDS’s AES-256 encryption to encrypt data. RDS stands for “Amazon Relational Database Service.” Amazon RDS encrypted DB instances using an industry-standard AES-256 encryption algorithm to encrypt your data on the server that hosts the Amazon RDS DB instances. After the data encryption, Amazon RDS handles authorization of access and decryption of your data with transparency. With the help of this feature, you don’t need to apply encryption to your application database.
User-Defined Privacy
In Bubble, we can protect our app’s data at the application level using user-defined privacy rules. It is a restriction that you can apply to your Bubble app’s data to control who has access to it. It maintains database records out of search results and controls which users can view and update all or specific fields and available file attachments.
In the Privacy section of the Data tab, you can define a new rule for the selected Data type. To define a new rule you have to click on the define a new rule button.
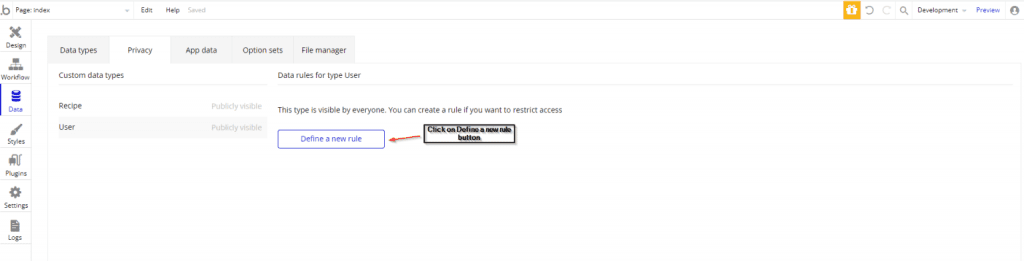
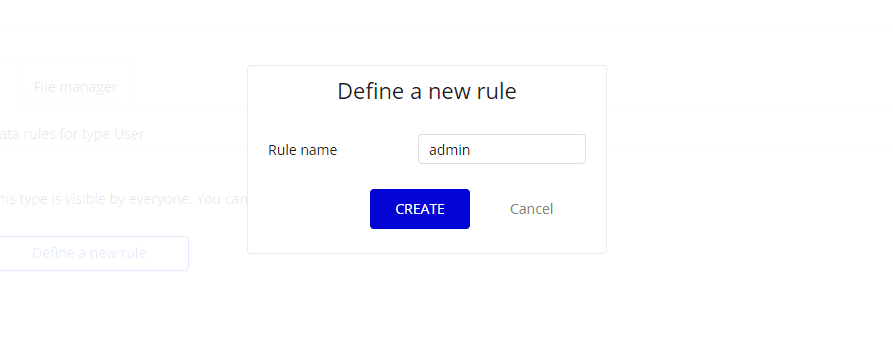
A Defile a new rule popup will open. Fill the rule name and click on the CREATE button.
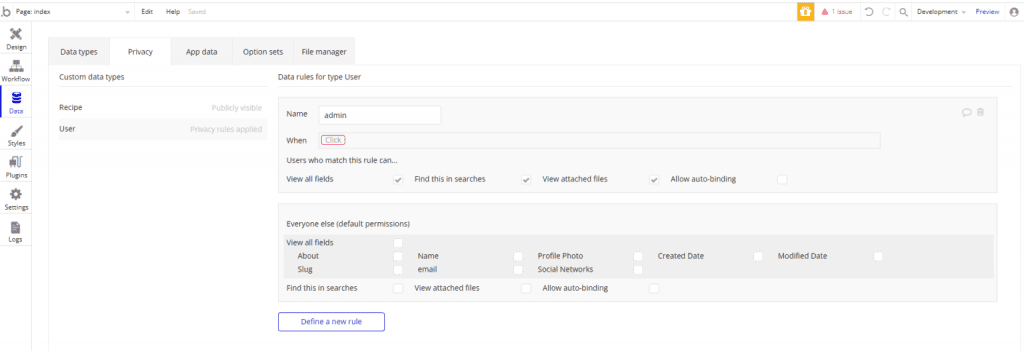
Now you have to write a condition on the “when element” and provide the permissions to the user who will matched the rule. Also you can provide default permissions for the users who will not in the criteria of the rule.
Conclusion
Bubble.io is a great choice for rapid web and mobile development projects, Bubble.io takes care of all the complexity of managing the infrastructure, data, and security so that you can focus on solving your business challenge.
We are a team of professionals with cross-domain experience and knowledge for building custom no-code apps in a secure and scalable way
.